Breaking down an elegant phishing attack using AT&T’s brand
Several weeks ago, KONTXT detected and stopped a phishing campaign over MMS messaging before impacting customers. This fraudulent campaign was in stark contrast when compared with other phishing/smishing campaigns we regularly detect and block on daily basis. It looked good, functioned well, with proper grammar– as professional as any marketing campaign from a major brand. This campaign actually started at the end of 2021 over SMS and then migrated over to MMS with enhanced images and targeting techniques. KONTXT stopped them all.
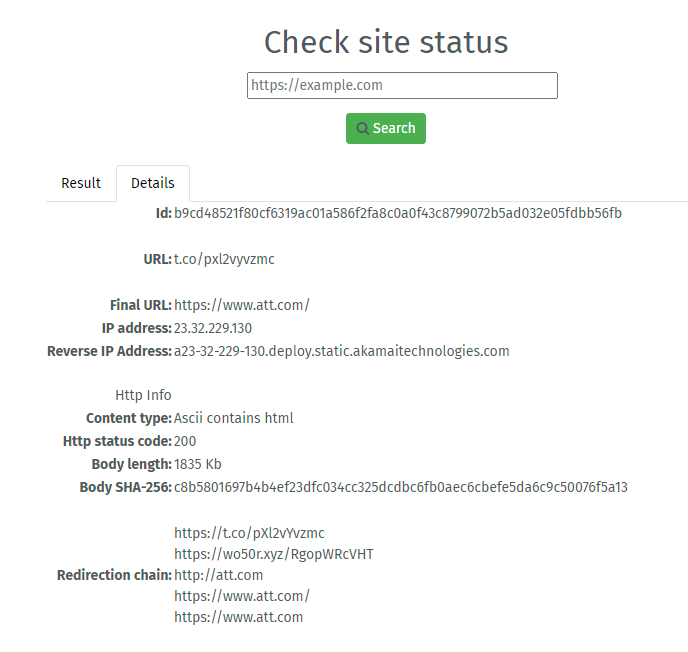
Most phishing campaigns attempt to carpet bomb targets with text messages– with the hopes a few misspelled words would help them pass through the spam filters– relying on pure volume to nab a one or two percent conversation rate. This particular branch of a longer running campaign starts by using MMS which has been an historically under-protected route. The message itself included a professional looking image along with a plausible premise: thanking the customer for paying their bill. The call-to-action is also typical of a major brand: claim your loyalty reward. Once the user clicks on the included shortened-url, the criminals check the user-agent and route one way or another. If the user agent is a mobile web browser, the target is presented with a professional survey path; else, the user is sent to att.com. Let’s take a closer look.
Step 1: Image and URL sent to millions of devices

Step 2: User clicks and redirect logic executed
Using a desktop User-Agent, it redirects to the legitimate att.com web site. Is the UA is mobile, it redirects to: marvelousokay.xyz , where the actual scam begins.
URL Analysis:
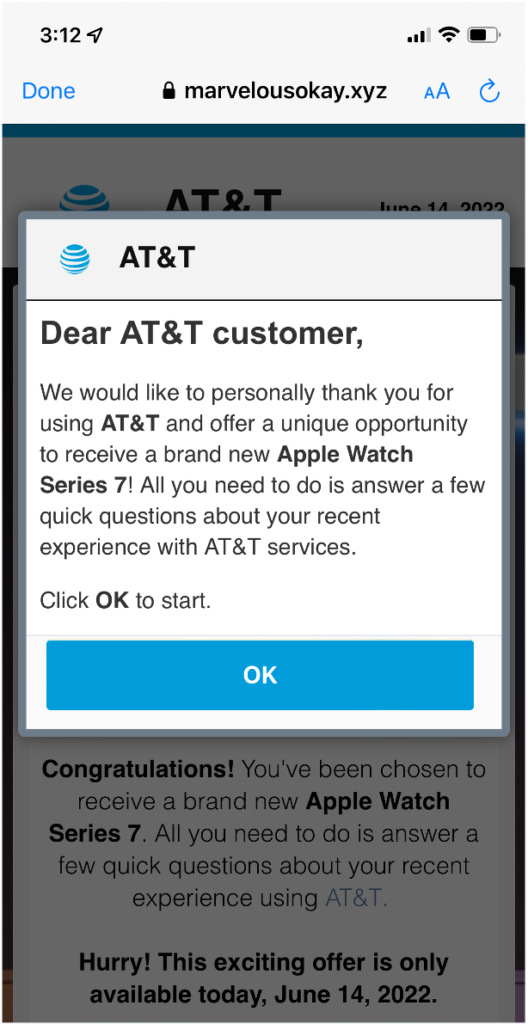
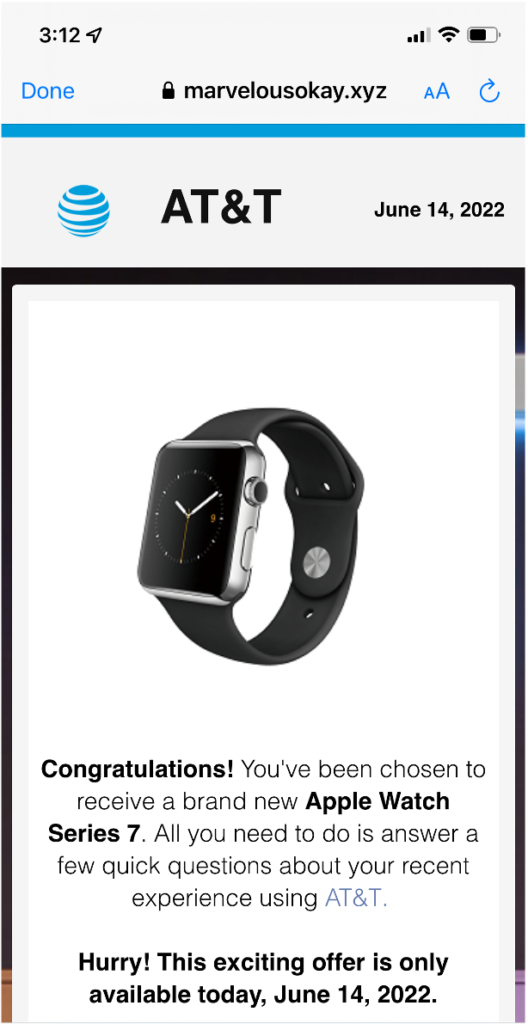
Step 3: Trick the user into giving up their information by presenting a professional survey
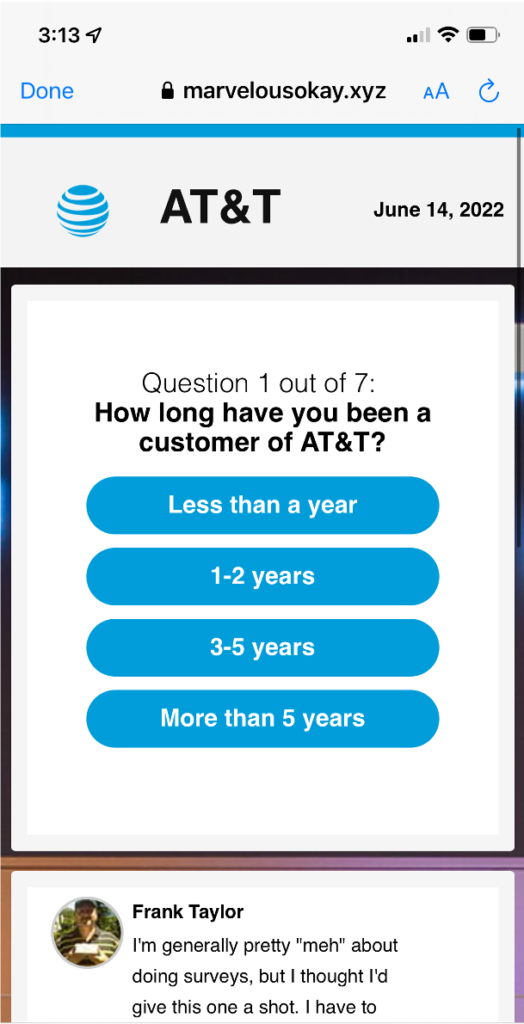
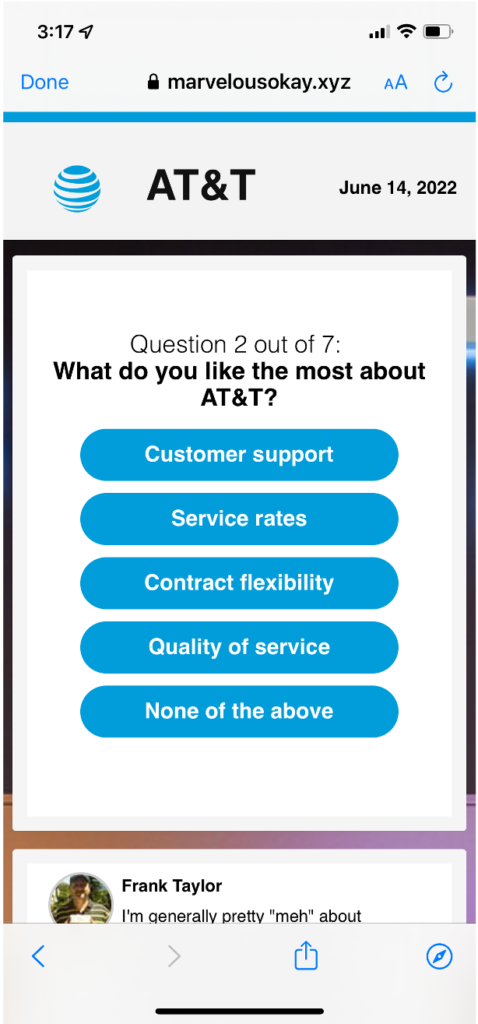
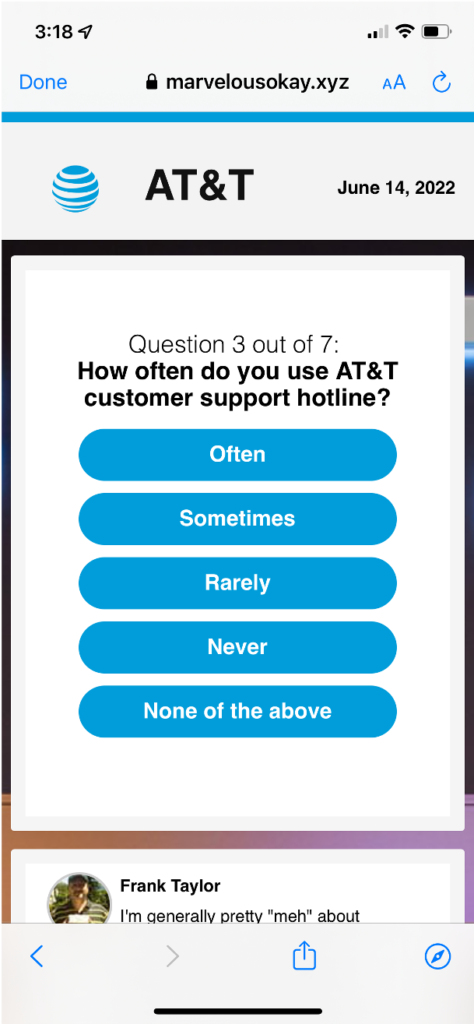
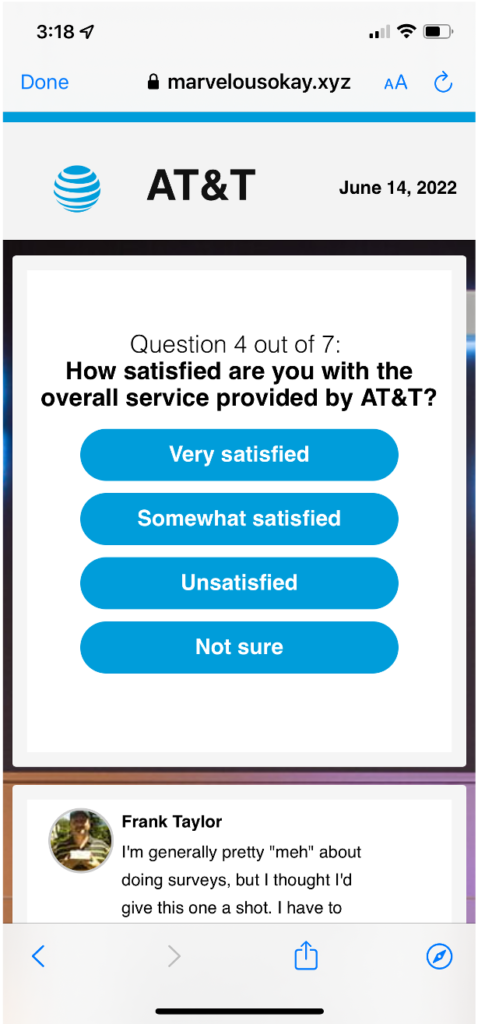
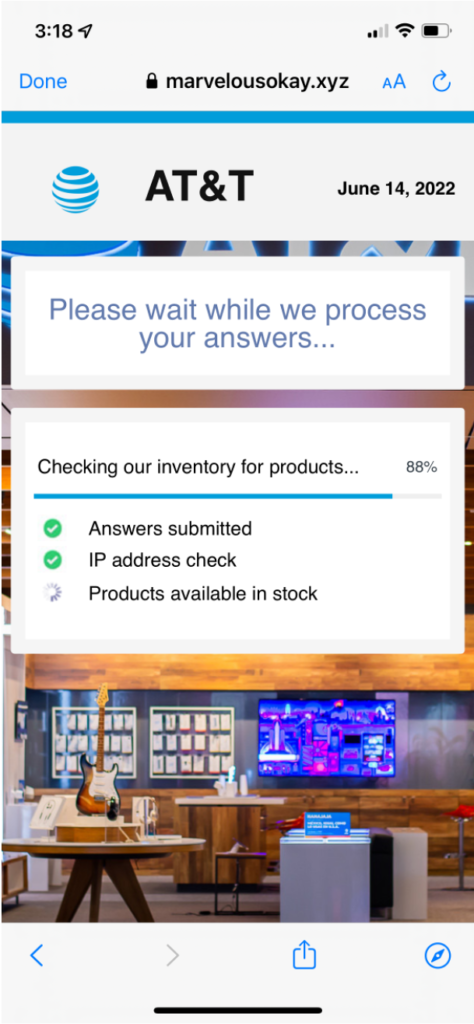
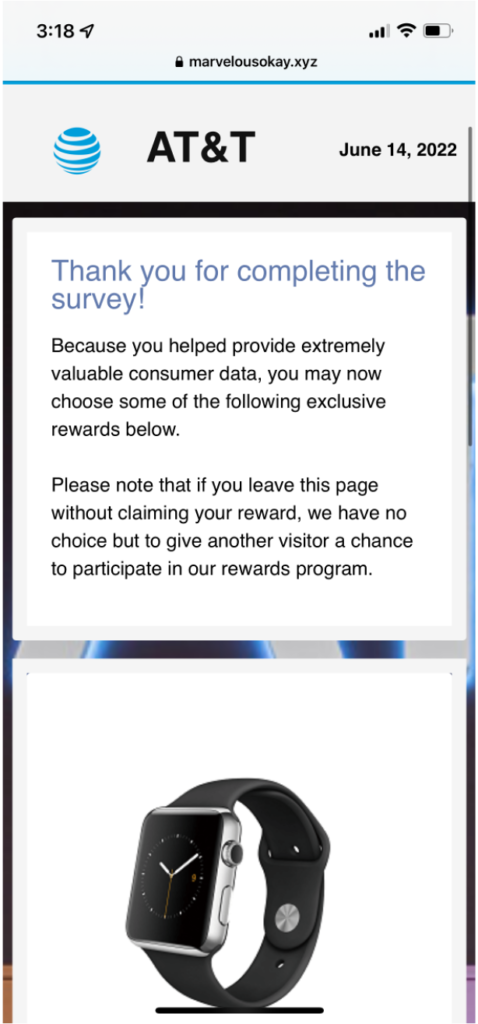
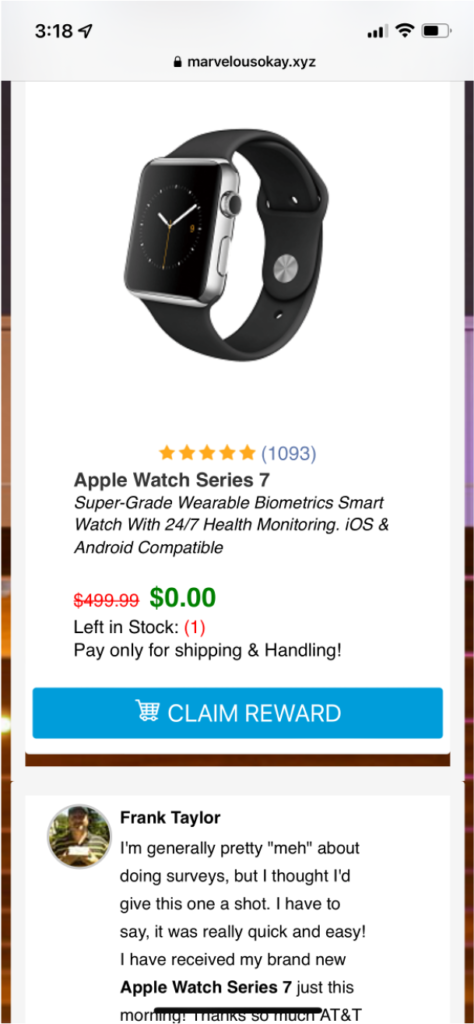

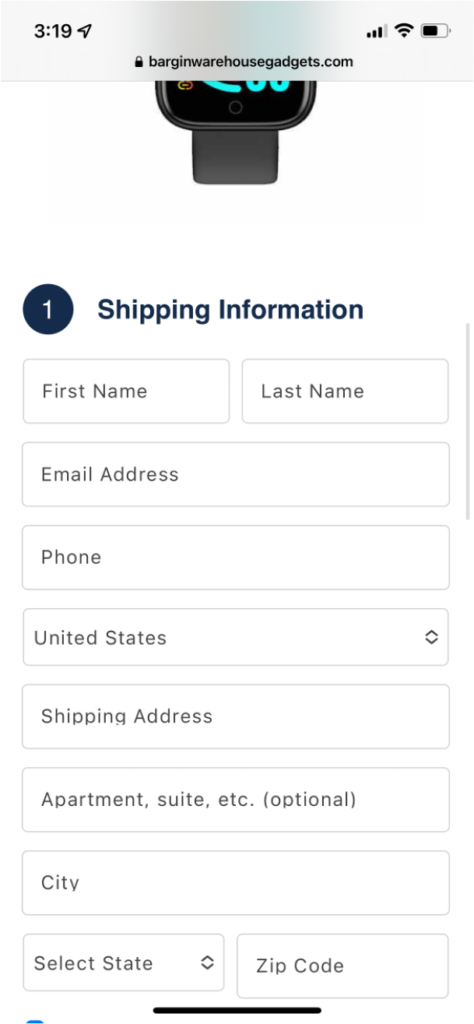
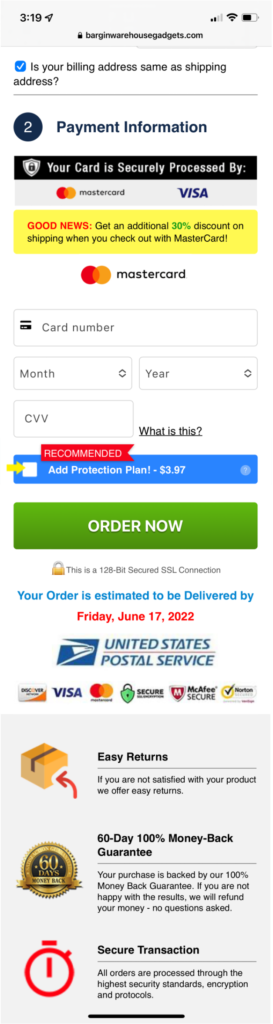
Step 4: Make Money
If the target completes the survey and then moves on to claim the loyalty reward, the criminals have some options. They have your CC number and can run charges against it, purchasing gift cards, electronics-for-resell, or cash back. They can bundle the CC numbers along with personal information and sell the database via Tor/onion marketplaces. They can keep the data and work these as leads for additional scams.
Step 5: Conclusions and SWAGs
57% of FTC reported fraud in 2021 happened over Voice and Text; imposter scams accounted for $2.3B in reported losses; beyond reported fraud losses, unwanted calls and messages erode subscriber satisfaction and trust in carrier services. The average open rate for text message marketing campaigns is 98% vs 20% over email.
The KONTXT Anti-spam/Anti-fraud service for SMS, MMS, RCS identified and blocked these messages on routes that we protect, including AT&T and Verizon inter-carrier pathways. Unfortunately, on-network paths that were not protected by KONTXT saw these messages go through. As of the writing of this article, KONTXT stopped over 6 million of these messages from reaching their intended recipient. Our estimate (SWAG) is that an additional 6 million messages made it to the end user via On-Net routes and other routes not protected by KONTXT.
If 1% of the recipients were hooked by this phishing expedition, the criminals were able to collect 60,000 leads. With the average going rate for a valid credit card plus user information of $16.50, the criminals could have earned about a million dollars from this single branch of a broader campaign. Not bad for a few hours work.
This is just one small example of the countless fraud that is carried out by foreign actors targeting US citizens– with an uptick in fraud targeting Canada, UK and Germany. KONTXT uses advanced machine learning techniques that continuously monitor for and stop this fraud from reaching consumers. You can do your part by educating your loved ones on the dangers of message spam.
Want to learn what happens to your data after being stolen by a phishing campaign? Your contact details, mobile phone number, email address, name, address can be used as leads to power fake/imposter call centers. Jim Browning on YouTube takes the next step by exposing these call centers and helping stop rampant fraud from impacting our friends and family.
Here’s a primer on how it works:



Thanks for your blog, nice to read. Do not stop.